
Protecting Automation Workshop
Secure default installation of Automation Workshop. Use built-in security features and Windows settings to protect your workflows.
Discover the ultimate Security Guide for protecting Automation Workshop. Learn the Best Practices and essential Windows Settings to safeguard your important data and ensure a secure experience.
This comprehensive guide provides tips and step-by-step instructions for enhancing Automation Workshop security, covering topics such as securing sensitive data, managing user access, and implementing robust authentication measures.
Watch a video
Watch a quick video introduction of Automation Workshop. Now, it is easier than ever to automate your repetitive and mundane workflows · Explore more demo videos
Overview
While Automation Workshop is designed with strong security features out of the box, security is not just about software, it is also about the practices and policies in place to protect your systems. By default, Automation Workshop user interface and Task files are accessible to all users on a specific Windows machine for user convenience.
Understanding default settings
In a scenario where only a handful of administrators have access to the machine, this is not usually a problem. However, in a more complex environment where numerous users have access (while not all of them require access to Automation Workshop), it may be necessary to implement additional safeguards.

Remember that securing your data and automated workflows goes hand in hand with securing your Windows workstations and servers according to best security practices.
The main objective of this guide is to provide tips and advice to enhance the default security configuration of Automation Workshop and to help you understand how you can add extra layers of protection to your Windows machine.
User access
Controlling who has access to Automation Workshop is a vital part of your overall security strategy. The simplest, yet one of the most effective, measures you can implement is setting up an Automation Workshop password. This setting is easily accessible from the Automation Workshop options. By enabling the password, you ensure that only authorized users gain access to the Automation Workshop user interface.
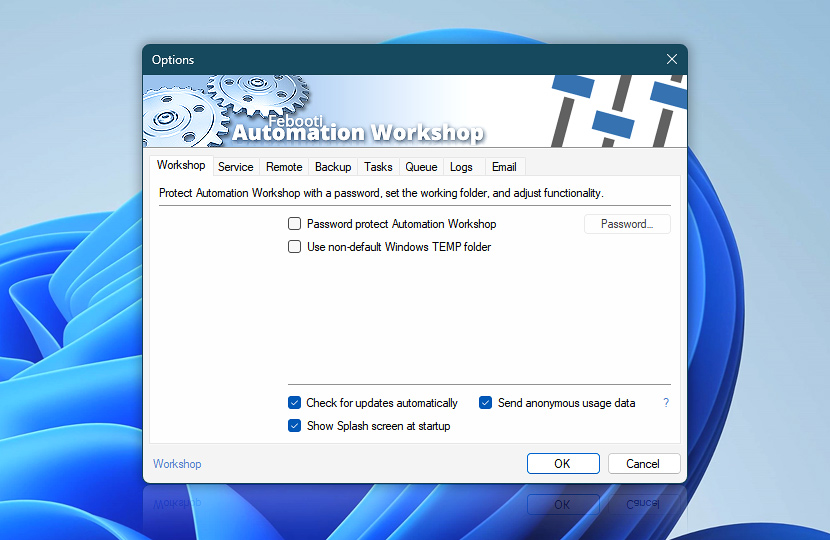
As you secure Automation Workshop with a password, your Windows system must also be protected by a password. This is crucial for preventing unauthorized access, even in cases where Windows configuration allows automatic login without requiring a password.
If you choose to utilize the Automation Workshop Remote Management features, available within the options, an Access Key is used instead of a password. By default, this Access Key is extremely secure and randomly generated for each machine. If changed by a user, for optimal security, it is advised that the Access Key must be at least 64 characters long. This ensures a necessary defense against unauthorized remote access attempts.
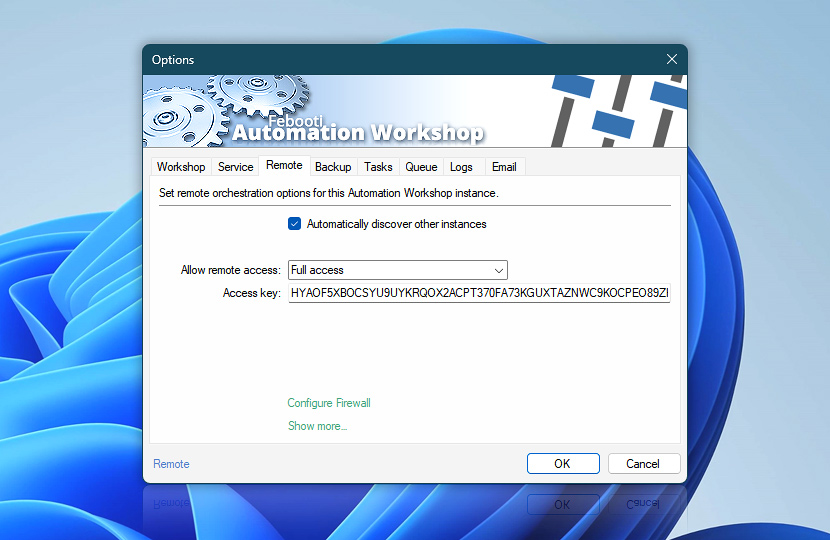
Upon setting the Password and the Remote Access Key, you should next consider configuring proper folder and Windows Registry permissions. These settings control who can access and modify your Automation Workshop workflows and related settings.
For detailed instructions on how to do this, refer to the sections on Folder Permissions and Windows Registry Permissions later in this guide. These steps will further enhance your Automation Workshop security and safeguard your automated Tasks.
Securing sensitive data
Handling sensitive data with utmost care is essential in ensuring the security and privacy of your automated Tasks. Whether your data is at rest (stored on your devices), in use (being processed or analyzed), or in transit (being transferred between devices or networks), it should be sufficiently protected to prevent unauthorized access.
One of the most effective and user-friendly measures to safeguard your sensitive data on Windows is enabling BitLocker on all your drives. BitLocker (available in all Pro and Enterprise Windows editions) is a built-in encryption tool in Windows that provides an additional layer of security, and it is completely transparent to end users.
It encrypts all data on the drive, making it unreadable to unauthorized users. If an unauthorized person attempts to access or use the data, they will find it scrambled and impossible to read without the correct encryption key.
In addition to BitLocker, server-level protections are crucial. All database servers (be it SQL or NoSQL) along with email servers, FTP servers, and cloud storage services should be protected with strong passwords. This fortifies the first line of defense against unauthorized access. Also, managing proper Folder Permissions and Windows Registry Permissions further enhances the security of your sensitive data.
Beyond system-level encryption like BitLocker, file-level encryption also provides crucial security. Automation Workshop employs industry-standard Advanced Encryption Standard (AES) wherever feasible, such as when communicating with other remote Automation Workshop instances.
Advanced Encryption Standard provides a high level of security and is recognized globally as a trusted method for protecting sensitive data (it is the industry standard for data encryption).
Moreover, when Tasks involve sending emails or transferring files to FTP, SFTP, or Cloud storage providers, Automation Workshop offers the ability to automatically zip files with AES encryption using the Zip Files Action. This provides an extra layer of security during data transfer, ensuring your sensitive data remains secure when in transit (even if it is necessary to use non-encrypted means).
Instant benefits
IT Process Automation using no-code tools is a new paradigm shift. People are creating amazing automated solutions without writing any program code. The automated workflows are created rapidly, thus reducing the initial costs, as well as improving your ROI in the long run.

Automation Workshop is an awesome piece of software. It will save us thousands of man hours this year alone!—Chuck W.
Authentication
A critical aspect of any communication protocol is proper authentication. This ensures that the identity of a user, system, or device is verified before it can access the resources it is requesting.
In the context of Automation Workshop, when your automated workflows connect to remote servers using industry-standard communication protocols such as FTP or SMTP, user credentials are sent in a format defined by RFCs (aka Request for Comments).
However, these formats are not always fundamentally secure. Therefore, it is essential to safeguard the data in transit to ensure it can not be read by third parties. For instance, using the built-in Transport Layer Security (TLS) protocol can secure network communications effectively.
Securing network communications
Automation Workshop Triggers and Actions are designed to meet these security challenges. All Actions incorporate means of secure communication by using Transport Layer Security (TLS), or Secure Sockets Layer (SSL) for older systems. These cryptographic protocols are designed to provide secure communication over a network, ensuring your credentials and data remain protected during transit, even when credentials are sent in the plain text format.
These security settings are enabled by default to ensure compatibility with most systems. Encryption of network communications should remain active unless the network communication channel is already secure, such as when network communication occurs on a Local Area Network (LAN) or between virtual machines in the same data center.
Additionally, it is recommended to select the highest supported (for particular service) version of TLS encryption. Each successive version of TLS has increased its security, offering stronger encryption and protection against potential vulnerabilities.
The option to enforce the TLS version for emails is available in the AW Options or directly in the Email Action. Similarly, enforcing a stronger TLS version is recommended for FTP & Cloud services (FTPS, WebDAV, Google Cloud, Amazon S3, Backblaze B2, and so on).
Two-factor authentication · 2FA
If a communication protocol supports two-factor authentication (2FA), Automation Workshop allows the enforcement of even stronger authentication solutions.
For example, an SFTP connection can be configured to require both user credentials and an SSH private key. Similarly, an FTPS connection can be set to require user credentials along with a client certificate. These security measures add additional layers of security to fortify your systems and data.
Folder permissions
To fortify the Automation Workshop setup, proper folder permissions can be set. This is particularly important as Automation Workshop Task files (workflows), Log files, and Global variables are stored on disk. Default location of these resources:
- C:\ProgramData\Febooti Software\Febooti Automation Workshop\
The default folder permissions allow all users on the system to access these files. If your use case does not require such broad access—for example, if only one user needs access to Automation Workshop—then permissions can be modified accordingly.
To change permissions, assign reading, writing, and modification rights to only that one specific user and to the built-in System user (NT AUTHORITY\SYSTEM). The System user requires access because the Automation Workshop Service runs under this user.
Alternatively, if all administrators on your system need access to Automation Workshop, you can change permissions to allow reading, writing, and modifications for the Administrator group and the System user.
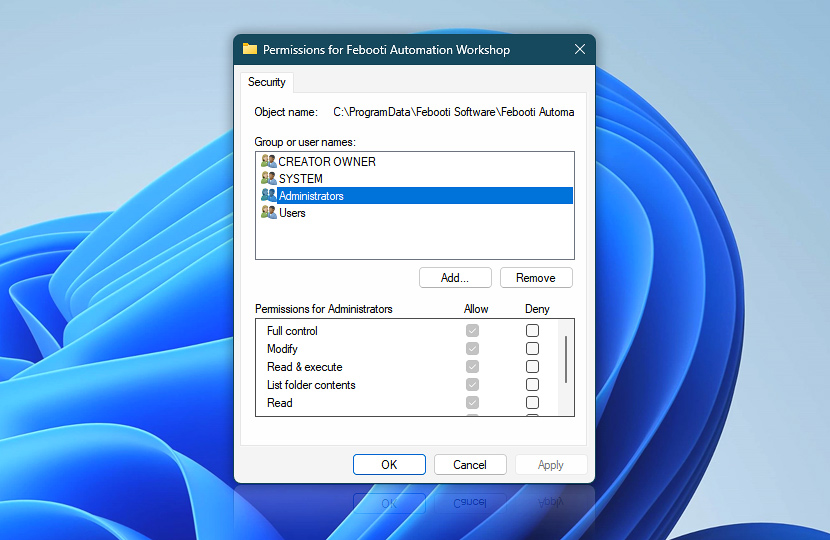
In addition to these changes, you may want to consider altering the folder permissions for the Automation Workshop installation folder for enhanced security. If, for instance, you wish to restrict access to Automation Workshop to a single administrator, modifying permissions for the installation folder would be a reasonable step. The default installation path is:
- C:\Program Files\Febooti Automation Workshop\
For more information on data and installation paths for these systems, please consult the Installation folders and files.
The default setup is designed to accommodate any user for ease of access, and these modifications are just further enhancements to optimize Automation Workshop for your particular requirements.
Registry permissions
Just as with Folder Permissions, it is important to align the permissions of the Windows Registry section for Automation Workshop. The Registry key "Automation Workshop" is located in the "Computer\" path. The permissions for this key should be adjusted to be in accordance with the permissions assigned to your folders.
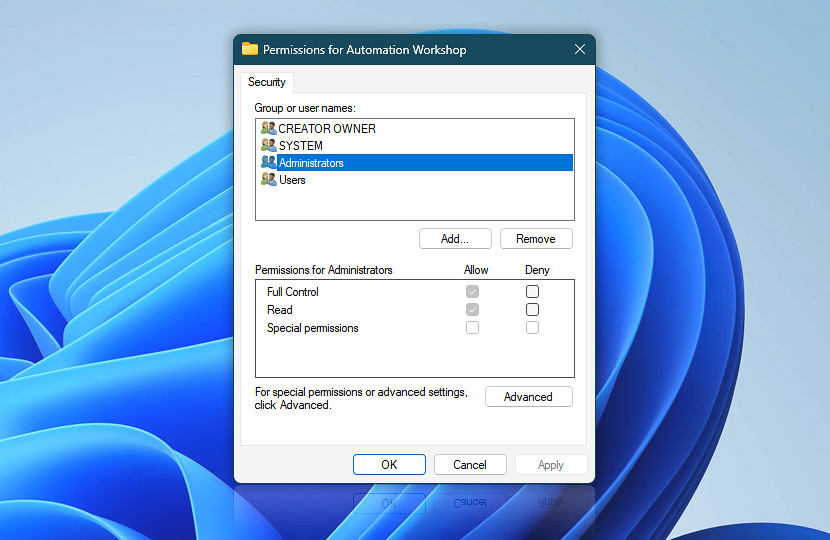
If, for instance, you have modified your folder permissions to only permit access to the Administrator group and the System user, the same set of users should be given permission to read and write the Registry keys. This continuity ensures consistency in your Automation Workshop configuration.
By managing Registry permissions, you are fine-tuning your Automation Workshop setup. This ensures a seamless operation of Automation Workshop to your user and security preferences. It creates an environment that balances convenience and safety in its operations.
Summary and recommendations
Having gone through the essential aspects of protecting Automation Workshop, it is clear that while the default installation is designed for ease of use and accessibility, customizing and tailoring settings to specific requirements can create a more personalized and secure environment.
From defining user access and securing sensitive data to setting up robust authentication measures, and adjusting Folder and Registry permissions, there are numerous ways to enhance the security of your Automation Workshop setup. Each step is aimed at creating an environment that best suits your use case and requirements.
It is always recommended to upgrade to the latest version of Automation Workshop as it contains important fixes and improvements. For an uninterrupted experience, we recommend using a subscription model as it allows seamless upgrades · Subscription vs. Perpetual licenses
Finally, a word of advice on overall system maintenance—while Automation Workshop strives to provide robust security features and configurations, it is equally important to maintain a clean and secure environment on your system overall.
Limit the installation of unnecessary software and ensure that all the software that is installed comes from trusted publishers. Keep your system lean and minimal. This not only improves performance but also limits the surface area for potential security threats, making for a more secure and stable Automation Workshop experience.
Remember, security is not a one-time setup but a continuous process of monitoring, updating, and improving. With these guidelines and recommendations, you have the tools and knowledge to make the most of Automation Workshop in a secure and efficient manner!
Awesome
- Automation benefits · learn more about the benefits of your daily task automation.
- State-of-the-art GUI · a truly zero-code solution for repetitive process automation.
- Awesome facts · learn some amazing tips & tricks about automation.
Jump in
- Getting started · basic concepts are explained.
- Triggers · define when to run a Task.
- Actions · define what a Task does.
Universally available
Advanced job scheduler—Automation Workshop works flawlessly on all modern 32-bit and 64-bit Microsoft Windows versions: Windows 10 · Windows 11 · Server 2016 · Server 2019 · Server 2022 · Server 2025.
Older Windows versions (such as Windows 8 and Server 2012) are not "officially" supported but should still work remarkably well. The underlying architecture of Windows is evolving and our apps are crafted to be backward and forward compatible.